Next Gen AI
Email+ Security
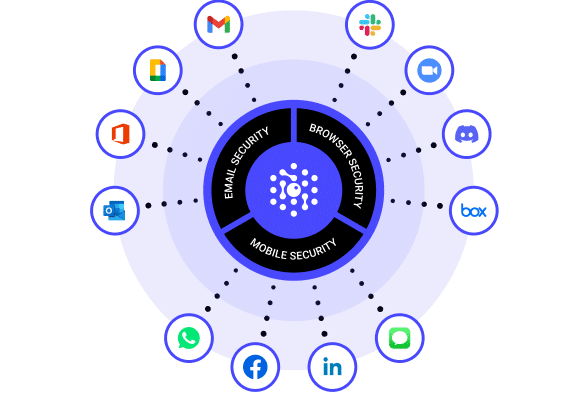
Our advanced AI technology protects against zero-hour spear phishing, BEC, smishing, and other socially engineered attacks in email, SMS, Slack, Teams, and other messaging apps.
Robust Multi-Channel Protection
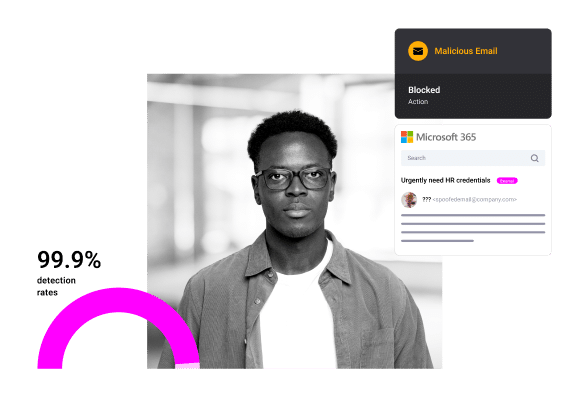
SlashNext’s Integrated Cloud Email Security provides a full defense-in-depth approach by supplementing Microsoft Defender with protection that is purpose-built to anticipate and stop the vast number of sophisticated zero-hour linked-based attacks, natural language-based attacks, malicious attachments and exploits that evade Microsoft Defender for Office 365.
SlashNext’s AI-powered platform combines natural language processing, computer vision, and machine learning with relationship graphs, generative AI and deep contextualization to thwart threats with a 99% detection rate, and the lowest false positive rate of 1 in 1 million.
Stop smishing and business text compromise with zero-hour protection against the broadest range of link based and natural language threats in any mobile application. Available for business, BYOD and home devices.
With on-device machine learning, users will benefit from detection without giving up privacy. Centrally managed for enterprise users, with multiple deployment options, incidents written to CMS, and supports all device types.
Stops zero-hour link and exploit threats with our integrated browser extension in all communication apps, including email, ads, social media, search, collaboration platforms, and more.
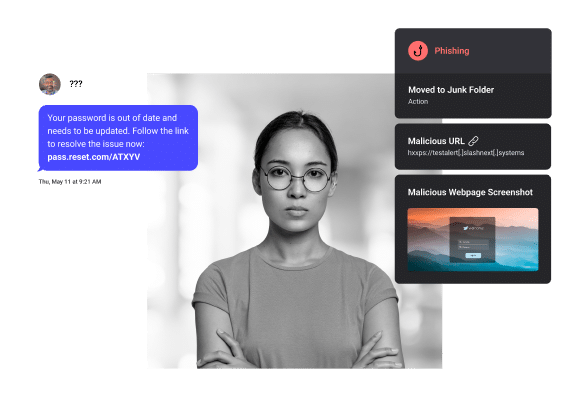
By blocking malicious sites in real-time, SlashNext protects users from more zero-hour threats including those that evade multiple layers of enterprise defenses.
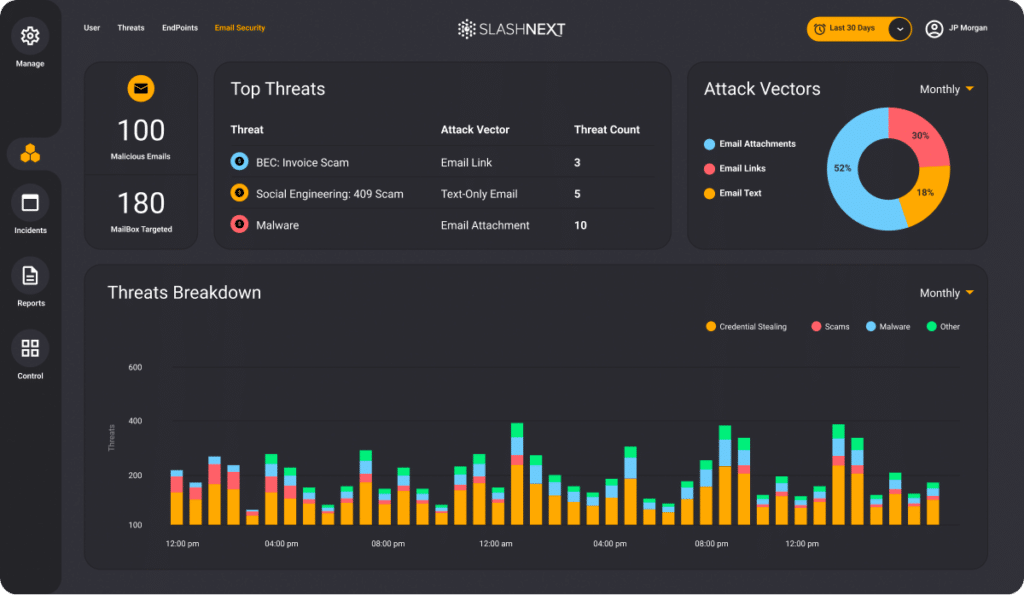
Cloud Management Console
The Most Advanced Email Security on the Market
Generative AI Detection Platform
- Powerful parallel predictive modeling using Generative AI
- Detects, predicts, and stops threats 48 hours before other solutions with efficacy gains superior to other leading solutions
Complete Multi-Channel Protection
- Complete multi-channel protection for Slack, Teams, Zoom, and 30,000 more communication apps
- Stops BEC, smishing, credential stealing, malicious attachments, exploits, and more
Fast API-Based Architecture
- Protection in minutes with cloud-native API integration
- Immediate protection with no operational maintenance or overhead
SlashNext for Microsoft 365 stops the broadest range of zero-hour attacks for total defense-in-depth security. Adding SlashNext ICES to Microsoft email security provides complete protection against targeted BEC, spear phishing, credential theft, malware and exploits in email, as well as SMS, social, collaboration apps.

DXC Technology Replaces SEG Solution with SlashNext Cloud Email Security
Trusted By Global Enterprises
8M Mailboxes, Devices and APIs Protected

Featured Resources
FEATURED REPORT
The Mobile BYOD Security Report
The growing use of personal mobile devices has resulted in many high-profile corporate breaches in 2022 and it is increasingly difficult for employers to ensure the security of sensitive corporate information.
Featured WEBINAR
How BEC Groups Exploit Generative AI to Launch Attacks and What’s Required to Stop Them
Learn how Generative AI can proactively anticipate potential BEC threats created using the same AI technology.
Featured White Paper
Microsoft 365 + Integrated Cloud Email Security
Due to the demands of the modern workforce, there has been an exponential shift in the use of native cloud email protection capabilities, like Microsoft 365, in the last 12 months.
See SlashNext Complete™
in Action
Meet with a security expert for a demo and learn how to set up a personalized trial to see the threats entering your organization.