Since the shift to remote work, attackers are capitalizing on the surge in new tools to aid remote workers as a way to steal credentials and ultimately exfiltrate data from an organization.
Such tools include Zoom, Microsoft Teams, Ring Central, and Google Meet. All of these platforms have seen a spike in usage since the Pandemic began. SlashNext Threat Labs continues to see new sites being registered, impersonating these common platforms.
Here is an example of a site impersonating Zoom asking a user to enter their email address and password or sign-in with other sources such as Google, Facebook, or corporate issued single sign-on services.
URL: (hxxp://zoomuserin(.)000webhostapp(.)com/)
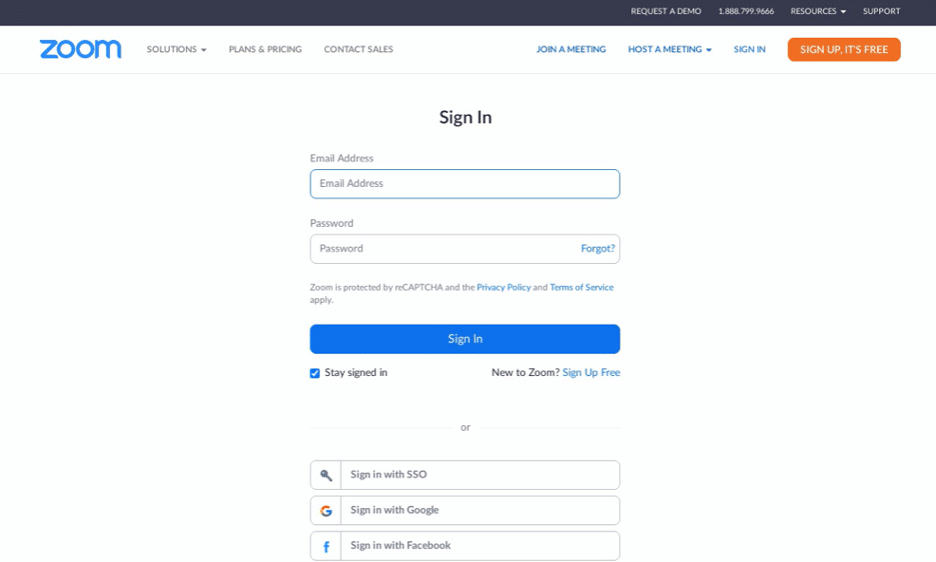
Over 95% of breaches start with credential stealing, according to Gartner. If users are reusing the same password on multiple work accounts from Zoom to O365 and Dropbox, it is easy to gain Zoom credentials and then use that to gain access to other platforms that share the same credentials.
Many employees have had to move from in-office operations to using technology at home to access corporate environments with limited time to prepare. Making them increasingly vulnerable to falling prey to giving up their credentials because they associate certain platform names Synonymous to remote work.
With 71% of companies using cloud or hybrid cloud email, according to Gartner Market Guide 2020, attackers see collaboration tools as fertile ground for credential stealing. SlashNext Threat Labs see a growing trend of malicious URLs that appear to be similar to a meeting invite being used to harvest O365 or G-Suite credentials.
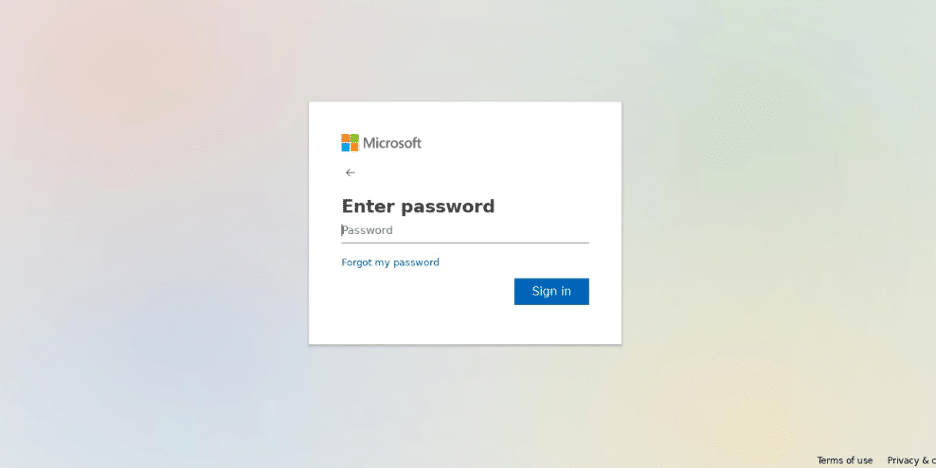
url: (hxxps://zoomorg6839(.)z13(.)web(.)core(.)windows(.)net/)
Here we have a malicious URL that looks very similar to the URL of a scheduled zoom meeting, but the landing page asks the user to enter their O365 credentials.
The average user simply trying to adjust to WFH is constantly inundated with new applications and tools to enable their remote work and might not think twice or find it strange why a Zoom URL asks for O365 credentials.
As the threat landscape continues to evolve, it requires a new approach to protect the ubiquitous user, and at SlashNext, we are keeping pace to ensure we provide end-to-end phishing protection.
Take advantage of advanced AI-driven phishing 2.0 protection with patented SEER technology, the industry’s largest phishing database, delivering 99.07% accuracy and one in one million false positives. SlashNext inspects billions of internet transactions and millions of suspicious URLs daily using virtual browsers to detect zero-hour phishing attacks across all communication channels– email, SMS, collaboration, messaging, social networking, and search services – up to 30 days before they are live. So, when phishing campaigns launch, the threats are already blocked by SlashNext, and users are protected immediately.
Test Drive the Service
SlashNext offers a free 14-day trial for companies that want to protect themselves today from phishing. For more information, please visit our product pages here: www.slashnext.com.


