Cybercriminals are Open for Business and Ransomware is the Daily Special
When it comes to spear-phishing and ransomware attacks, it’s time to think outside of the inbox and consider these (scary) facts:
- 80% of web application attacks result in credential stealing, Verizon 2021 DBIR (Data Breach Investigations Report) which is the leading cause of ransomware
- Attackers are using man in the middle (MitM), rogue browser extensions, social engineering, and malicious webpages hiding on legitimate infrastructure, to hack humans.
- 50,000 new spear-phishing sites go online each day, many on legitimate infrastructure like Spark[.]adobe[.]com, dropbox[.]com, onedrive[.]live.com app[.]box[.]com, and alchemy[.]com to just name a few
- Secure web gateways, URL filtering, legacy malware protection, browser isolation, and internet policies are all strategies to defend users from web threats, but they are struggling to keep pace with fast-moving web-based phishing threats, leaving corporations exposed to ransomware
Browser Extensions, an Overlooked Phishing Attack Vector
A browser extension adds functions and features to improve productivity and many are used daily to access critical business applications. The Chrome Web Store has over 180,000 extensions, ranging from productivity tools to shopping, games, These extensions install quickly and easily, and once they are installed, they save me time and effort. The appeal and adoption of browser extensions to consumers are naturally attracting the attention of cybercriminals.
Browser extensions can only be downloaded from their official stores. They are vetted by Google, Microsoft, and Safari before they can be listed for download. If this is the case, how do malicious extensions make their way into the official stores? There are many reasons, but here are a few:
- Browser extensions can be hijacked. All major web browsers, including Google Chrome, automatically updates a user’s installed browser extensions when new versions are available. When a developer’s account is compromised, it can be used to push malicious updates to already installed extensions, as was the case with a popular Web Developer extension for Chrome
- Browser extensions can be sold. Developers are approached by companies with offers to buy their extensions. Once an extension is sold, the new owners can update it with malicious features and upload it to the Chrome Web Store, and all the existing users are now using the new company’s version.
- The initial vetting process is not perfect, allowing some malicious extensions to bypass the safeguards and get listed
Users download the extensions from the official app stores, but the journey doesn’t always begin there. SlashNext’s Threat Labs found that users are directed to the extension stores through ad networks that appear on benign websites and search results. The ad networks, typically with multiple redirects, takes visitors to a lure page with an install/continue button (Figure 1). Clicking on the continue button opens the official Chrome Web Store (Figure 2). Users assume the extension is benign, since it’s from the official store, and install it without realizing what lurks beneath. Once a malicious extension is installed, it can do anything. It can insert advertisements into your search results, redirect your search traffic to phishing webpages, and it could even function as a keylogger to steal your MS O365 login credentials.
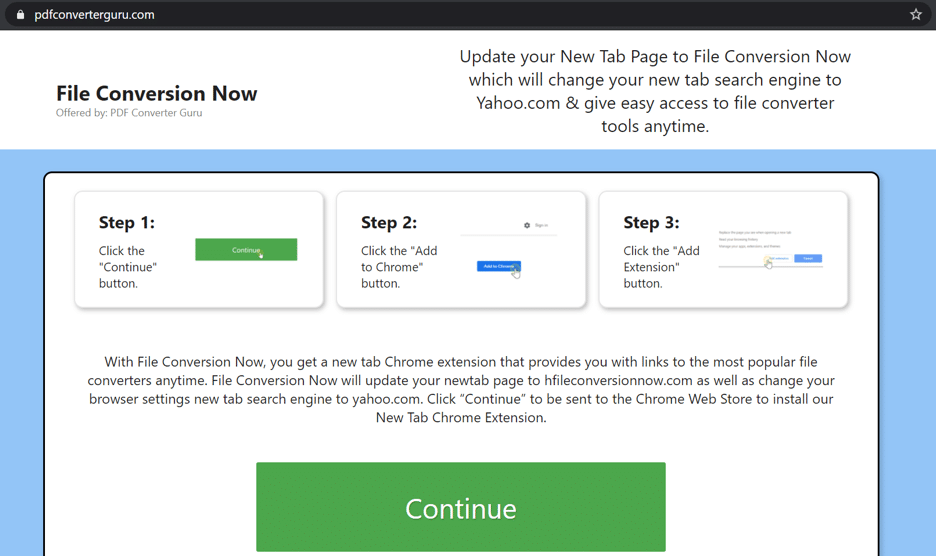
Figure 1: Ad Network Lure Page
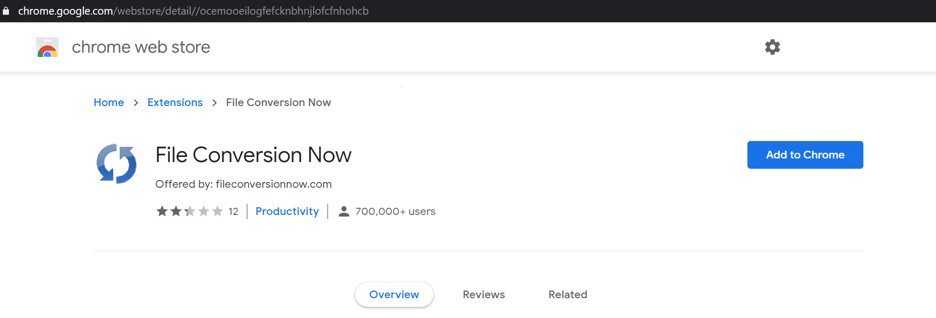
Figure 2: Chrome Store Malicious Extension
SlashNext sources over a 10 million URLs and internet transactions daily, from passive DNS feeds, phishing traps, hardware sensors, and suspicious ads networks, just to name a few. Our Threat Lab has uncovered over a thousand rouge browser extensions in the official extension stores. Our phishing protection solution prevents users from downloading rogue browser extensions while reinforcing positive user behavior. When our solution blocks a threat, we display a screenshot of the lure page and a detailed description of the blocked threat, to always remind users to be vigilant (Figure 3).
Figure 3: SlashNext Block Page with Screenshot of Malicious Browser Extension
SlashNext Browser Phishing Protection shields employees from live phishing sites with a lightweight browser extension available for all major browser. With a browser warning and safe preview, users who attempt to browse to a malicious site are blocked and receive an informative warning page allowing them to access a safe preview screen shot of the blocked page along with detailed information about the threat. Users can also report the incident and request support.
The Threat to Enterprises
Browsers, generally speaking, are quite secure and getting more so all the time. With improved software design and regular automated patching, zero-day browser exploits are getting rarer. The difficulty is that browser users are being tricked into adding browser extensions through a variety of very convincing and effective phishing tricks. This is causing major problems for enterprises today. These attacks typically come from phishing pages embedded with file-less HTML “malware”, which are difficult to track and trace. The rogue code is comprised of HTML5 and JavaScript code that runs as part of a browser extension, as mentioned earlier. The threat to the enterprise is that some of these extensions can run as spyware, steal user credentials, and enable data exfiltration to threat actors.
Once a user’s credentials have been compromised, the threat is further mobilized and can be catastrophic to the enterprise. Breaches are tremendously costly. It’s not just loss of critical business or customer data, but there’s risk of loss of IP, shareholder value, lawsuits, financial payouts, and more. These are just a few consequences a company can face when their employees fall victim to phishing attacks.
Join our webinar on July 29th at 10 AM PT Phish Stories 7: Browser is the New OS and Attackers are Open for Business with SlashNext Founder and CPO Atif Mushtaq, SlashNext CEO Patrick Harr, and Eric Quinn, CIO C&S Companies, to explore techniques hackers are using and real-life examples of how these attacks are getting past current defenses.
Register today /webinar-phish-stories-7/


