Cloud Email Security
Modern cloud email security stops the sophisticated email attacks like BEC, credential stealing, ransomware, and malware threats to reduce the risk of a data breach.
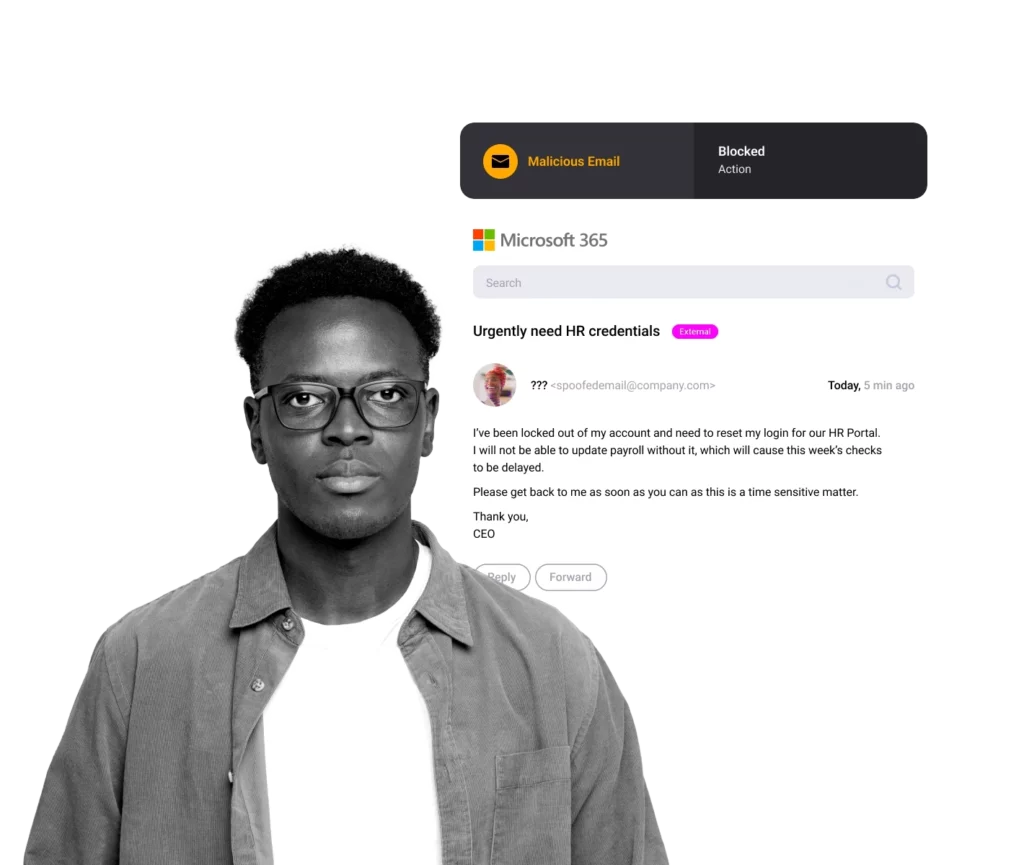
Legacy Email Security Fails to Stop Sophisticated BEC Threats
Email Phishing
91% of all attacks start with targeted spear phishing email attacks. Credential theft is the critical first step in a successful breach.
Sophisticated BEC
With automation and AI technology, BEC and spear phishing can easily adapt until successful.
Data Breach Cost
The average global cost of a data breach is $4 million with losses exceeding $10.3 billion annually.
Cloud Email Security That Stops Threats Others Miss
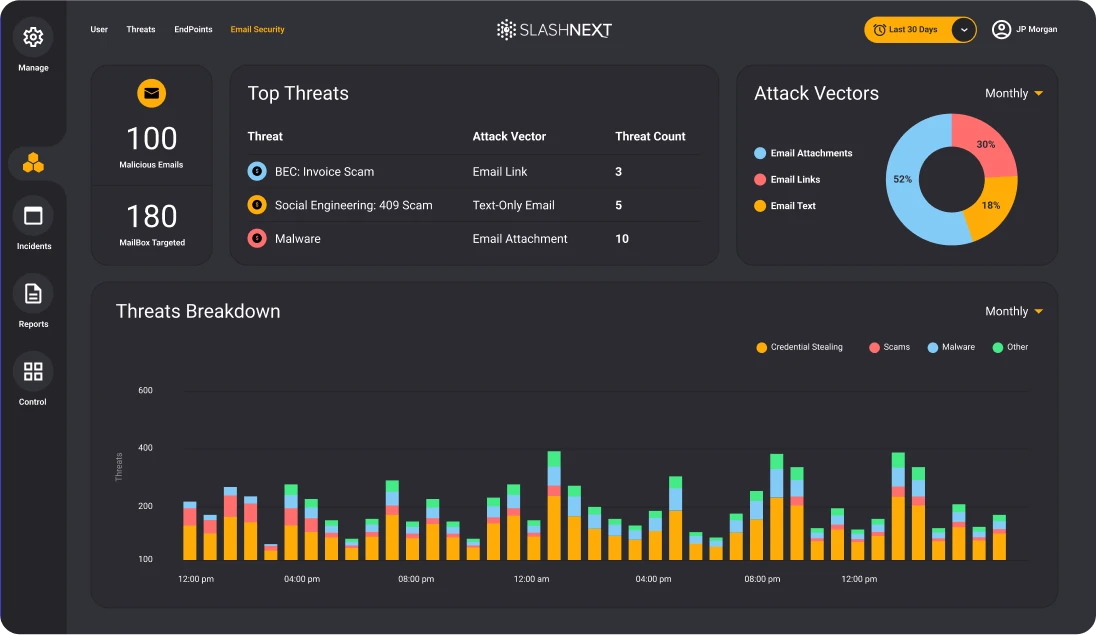
Best Zero-Hour Link, File and BEC Detection
Quick and Easy Implementation
Comprehensive Management and Controls
Threat Investigation and Reporting
How SlashNext Stops the Widest Range of Attacks from Entering Your Organization
SlashNext Generative AI Delivers Powerful Detection
SlashNext uses Generative AI to stop email threats that compromise users and lead to a data breach. Stop credential stealing, BEC, spear-phishing, legitimate link compromise, social engineering scams, ransomware and malware in real-time with fast 99.9% detection rates and one in 1 million false positive rate.
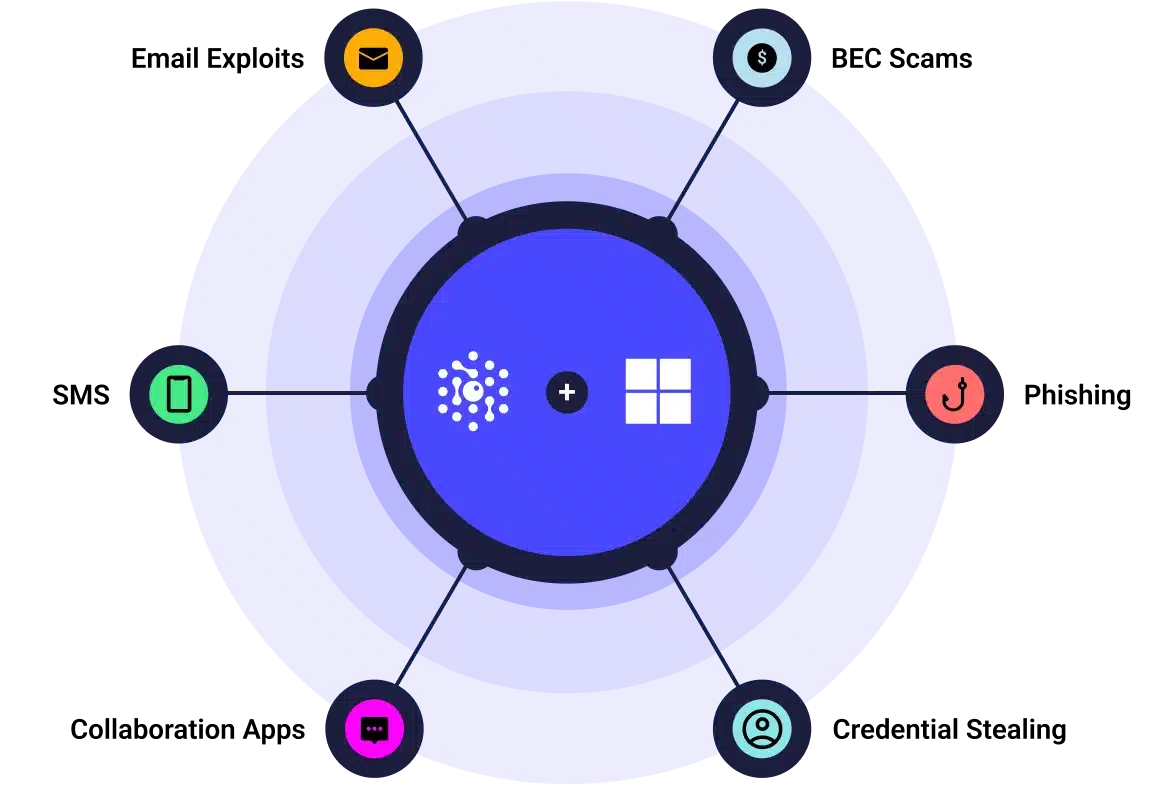
SlashNext + Microsoft, Better Together
As a trusted MISA certified partner with Microsoft it takes five minutes to instant detection of BEC, credential stealing, malware and more, by securely authenticating to the Microsoft Graph API using OAuth.
SlashNext works closely with Microsoft to deliver unmatched security solutions including integrated cloud solutions that can be purchased in the Azure Marketplace.
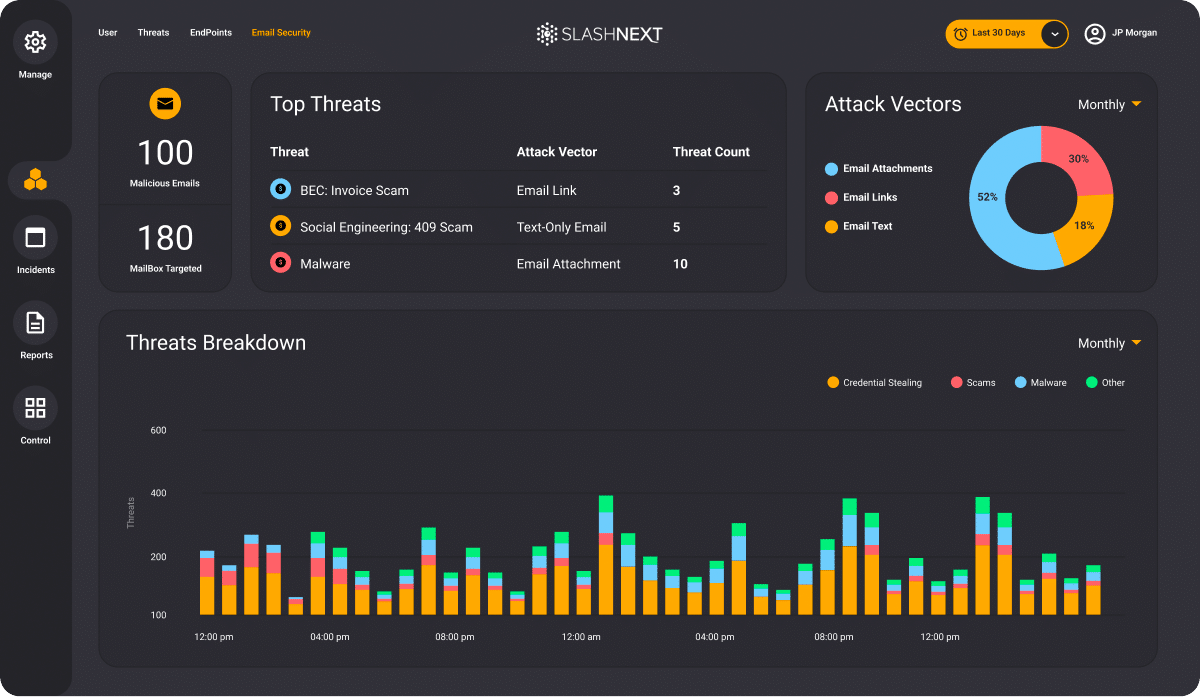
Cloud Mangement Console
SlashNext HumanAI™ Defends Against Advanced
Business Email Compromise
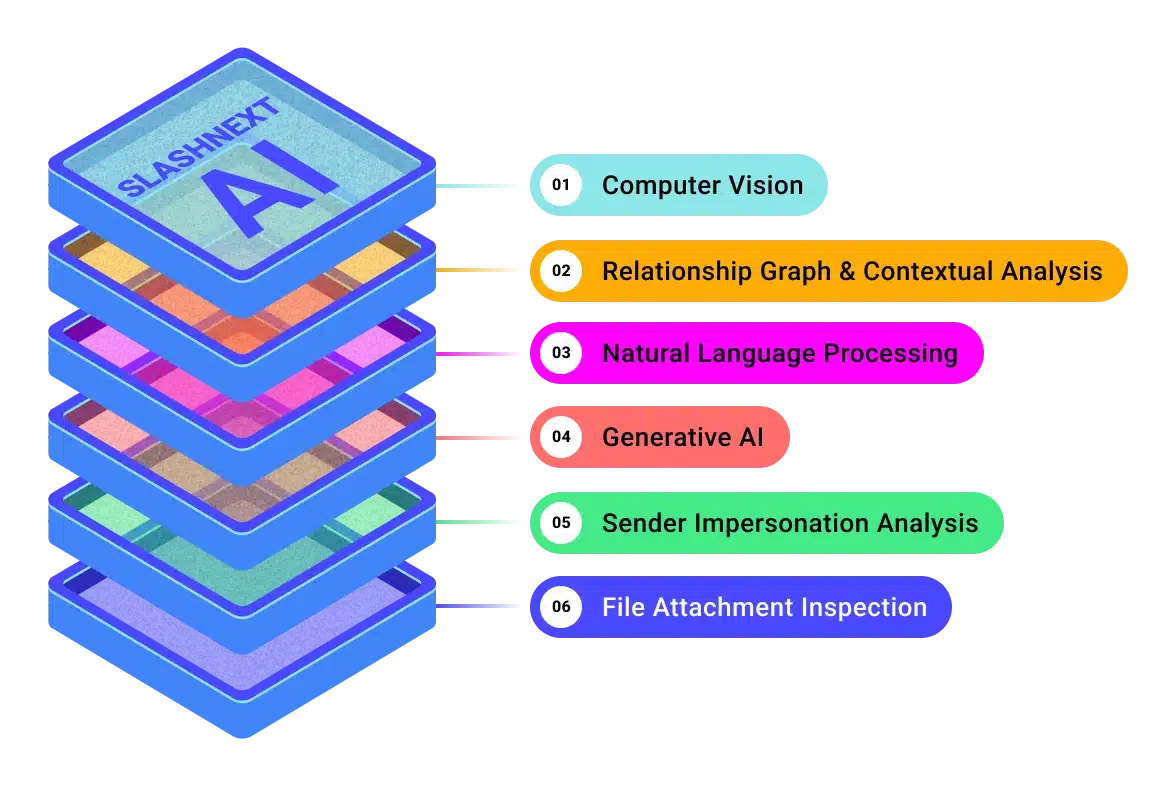
Relationship Graphs & Contextual Analysis
Baselines known-good communication patterns and writing styles of employees and suppliers. This provides insight into expected behaviors like invoicing and communication frequency.
AI/ML effectiveness depends on the ability to continuously learn to detect unusual communication and conversation style of BEC attempts.
Natural Language Processing
Analyzes text in email body and attachment for topic, tone emotion, intent, and other manipulation triggers associated with social engineering tactics.
A sense of urgency, unusual writing style, high emotions, personal or banking information are hallmarks of BEC attacks.
Generative AI for Advanced BEC Detection
Auto generates new BEC variants from current threats using Semantical Clones.
By extracting topic, intent, emotions and style of a BEC, the generative AI will create clones to all possible ways a human can write a similar email. This data trains the neural network how to detect thousands of variations of these BEC attacks.
SlashNext Delivers Best in Class Results on Day One
5 mins.
To set-up and configure service using the Microsoft Graph API
99.9%
Detection rate with 1 in 1 million false positives
2x more
Blocks two times more than competing supplemental solutions
1 hr.
Incident caught within 1 hr. for incredibly quick time to value
46%
Patient-zero email attacks detected by SEER™ Live Scan
48 hrs.
Detection advantage vs other threat engines
Stop The Attacks That Impact Your Business
Social Engineering, Scams and Fraud
Deception to manipulate users into divulging information for misuse.
Trusted Services Compromise
Uses trusted domains to obfuscate cyber attacks to increase success.
Ransomware, Malware and Exploits
Intended to inject code, take-over browser canvas or download malware.
Malicious Attachments
Malicious HTML, PDF and Office files used to harvest credentials or download malware.
BEC, ATO and Supply Chain Attacks
Targets execs or financial teams to defraud a company for financial gain.
Credential Stealing
Cyber attack designed to steal passwords with the intent of accessing protected data.
Spear Phishing
Personalized targeted attack designed to trick users into a data breach or for financial gain.
Smishing and BTC
Using SMS text messages to trick users into divulging passwords or other PII for fraudulent use.
Related Resources
FEATURED WHITE PAPER
Microsoft 365 + Integrated Cloud Email Security
Due to the demands of the modern workforce, there has been an exponential shift in the use of native cloud email protection capabilities, like Microsoft 365, in the last 12 months.
FEATURED DATA SHEET
Integrated Cloud Email Security - ICES
Cloud email security for Microsoft365 to stop zero-hour BEC, credential theft, malware and more.
Featured Blog
State of Phishing Report Reveals More Than 255 Million Attacks in 2022
SlashNext analyzed billions of link-based URLs, attachments, and natural language messages in email, mobile and browser channels over six months in 2022 and found more than 255 million attacks…
See SlashNext Complete™
in Action
Meet with a security expert for a demo and learn how to set up a personalized trial to see the threats entering your organization.


