SlashNext Phishing Vulnerability Assessment and Remediation
A simple way to see what is evading your current email defenses. The secure assessment is easy to run with Google workspace and requires less than 10 minutes of setup time.
Start Your Phishing Vulnerabilty Assessment Today
Reveal and analyze phishing threats that evade your current defenses in your Google workspace, weblogs, or both. Completing the complimentary secure assessment is quick and easy:
- No hardware or software to install. Access SlashNext’s Secure Cloud Manager to begin the assessment
- Available for Google workspace
- Receive a personalized risk assessment report
- Meet with a security expert to review the results
- Easily deploy protection to target users
Privacy and security are very important at SlashNext. Please read our FAQs to learn how we handle security and privacy.
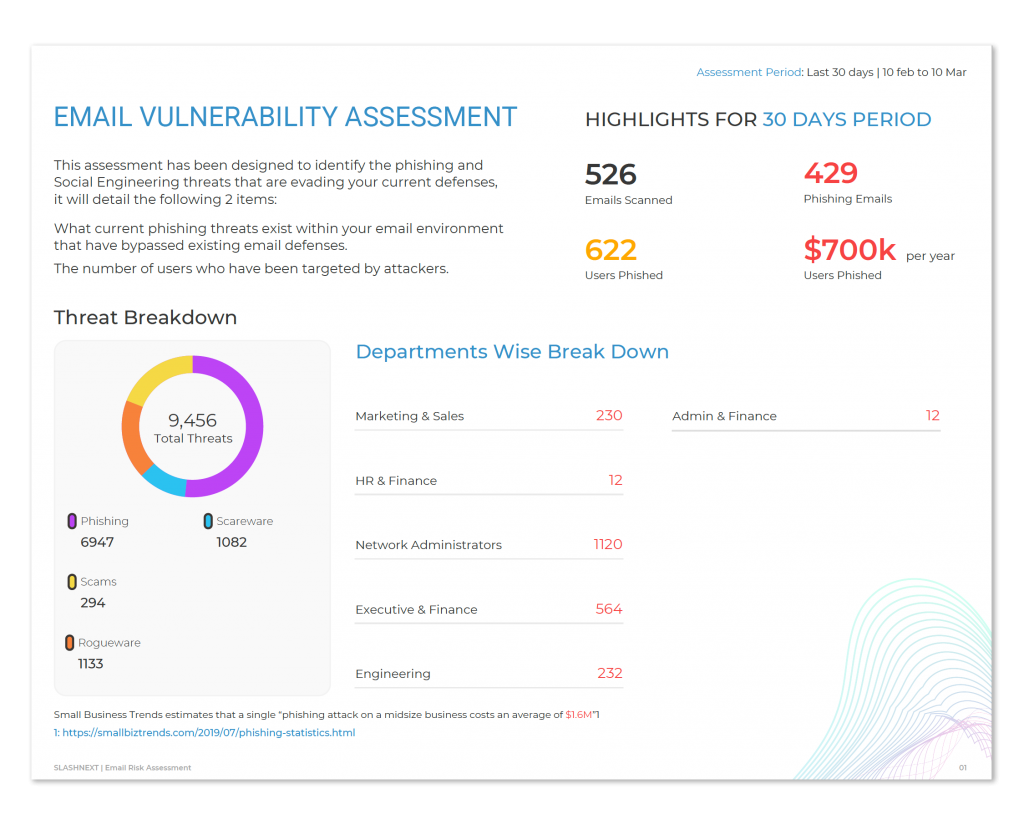
Real-World Threats Getting Through Current Defenses
Phishing attacks found in recent vulnerability assessments.
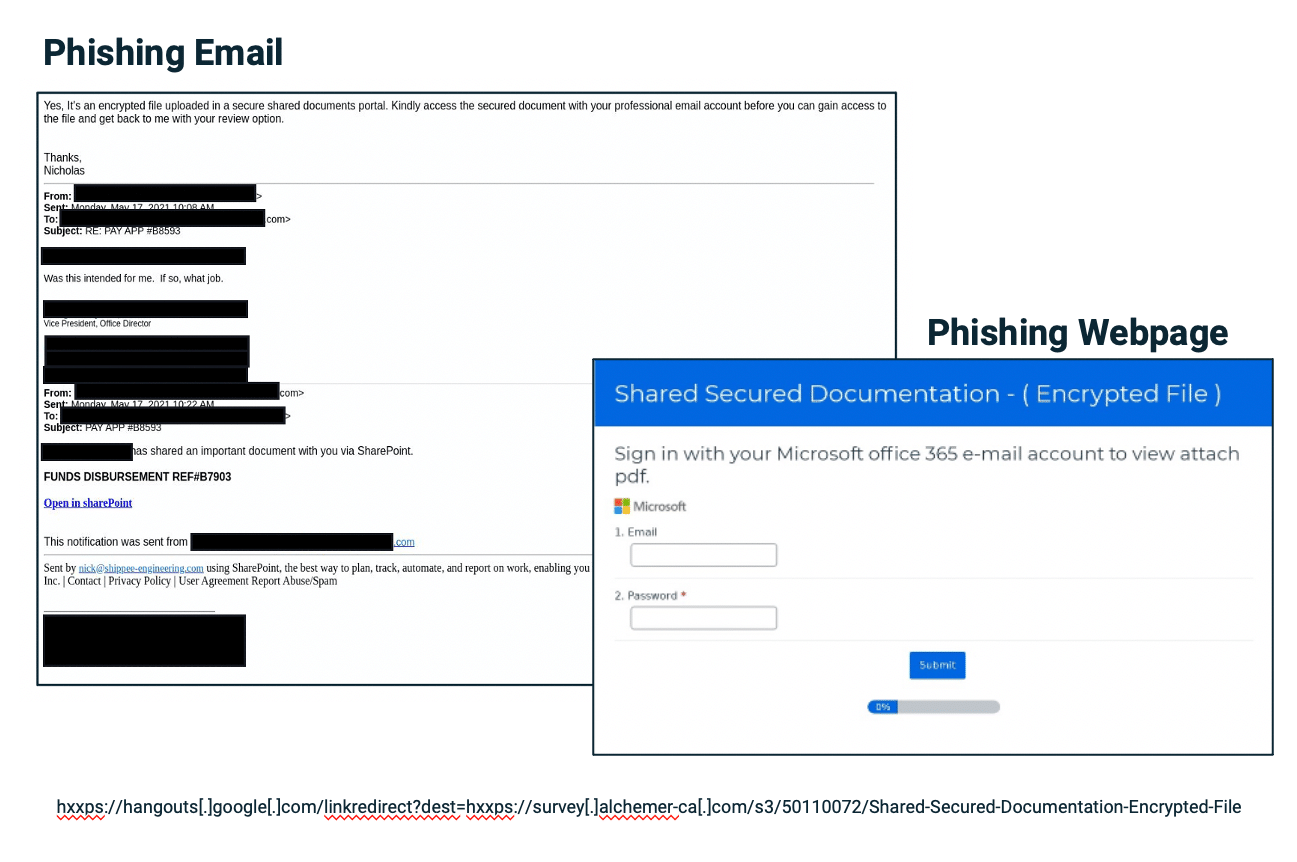
Spear Phishing Vendor Email Compromise
Target: Vice President
- User is fooled and bad actor continues the dialogue with the user, specifically requests O365 credentials
- Lure page mimicking Microsoft login
- Link hosted on legitimate infrastructure bypassing email gateway solutions
- Attack only sent to the Vice President
- Used email address of real employee from vendor
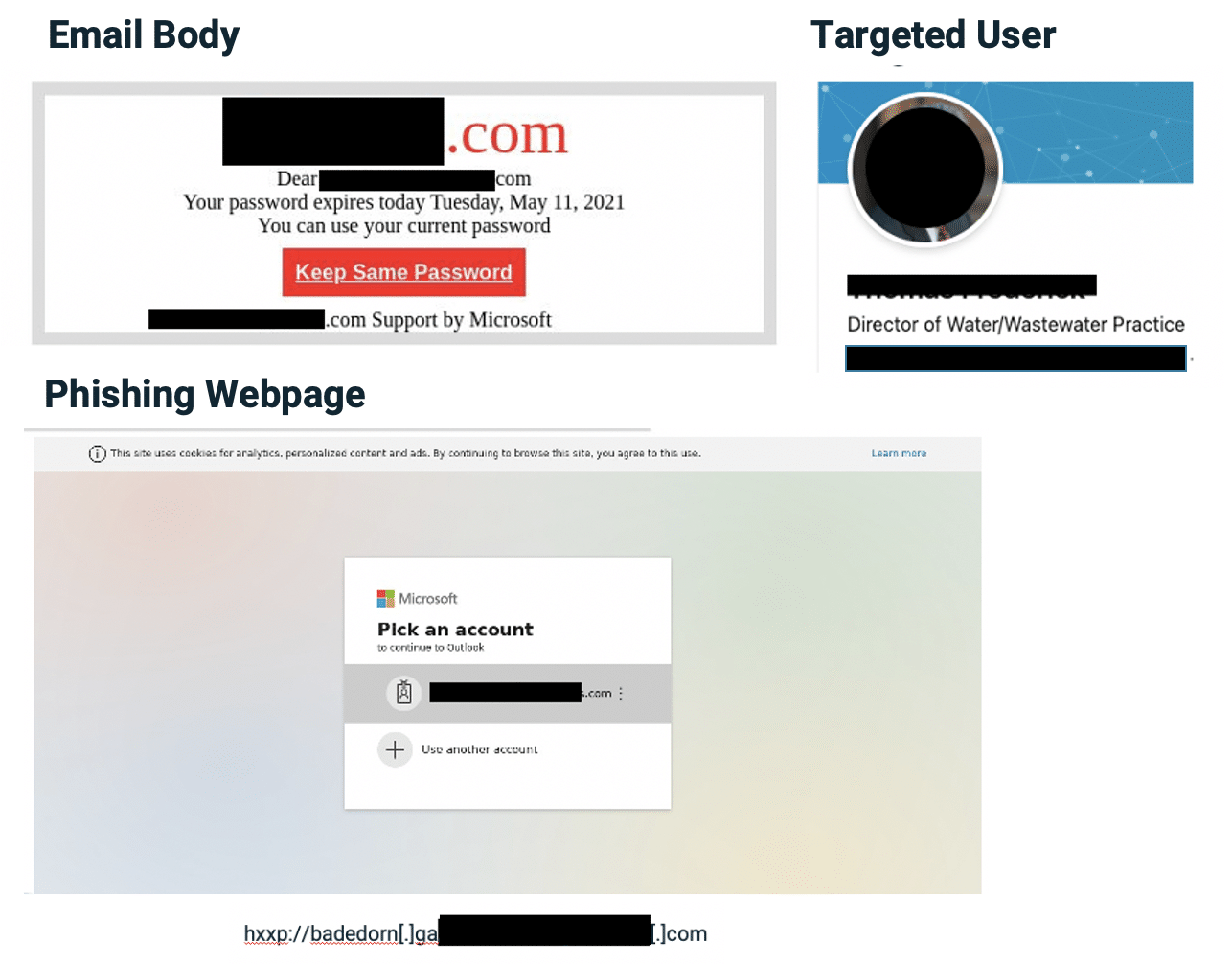
Spear Phishing Credential Stealing
Target: Director
- The phishing link was tailored for the user, and the credentials would have auto-filled into a fake Microsoft account
- Sent from legitimate ISP
Experience SlashNext Protection in Action
Request a free trial to see how SlashNext detects zero-hour threats in real-time and stop the attacks that impact your business.
6701 Koll Center Parkway, Suite 250
Pleasanton CA 94566
800.930.8643
info@slashnext.com
© All Rights Reserved, SlashNext, Inc.