Man in the Middle Attacks
The exact functionality of Man-in-the-Middle attacks is collecting and selling data. These browser extensions offer cybercriminals the perfect workaround for organizations that rely heavily on 2FA. SlashNext Threat Labs have observed malicious browser extensions that merely wait for 2FA to complete before launching. By design, once a browser extension is installed, it can access the browser’s complete canvas. Once logged in, the session is hijacked to capture whatever is being rendered on the computer screen. These extensions have the full power to do whatever the user is doing and seeing whatever is happening within that browser window.
All modern browsers such as Chrome, Edge, Firefox, and Safari offer third-party developers to enhance default functionality by writing custom code in the form of browser extensions. These browser plugins are not standard executables, but “apps” comprised of HTML, Style Sheets and Java Script code that runs inside browser memory. Once hooked into a browser, these plugins can use browser memory structures and resources to offer useful functionality. Browser extensions by design have full access to most of the browser’s resources and information being entered and rendered within the browser.
It was just a matter of time before cybercriminals realized that injecting malicious code inside browsers disguised as benign-looking browser extensions would not only give them unlimited access to all the data within browser, but also provide them with much needed cover from security systems that are designed to catch only malware executable and software exploits.
Because these plugins run inside browser memory, SSL encryption is not a problem for them. In order to bypass Two Factor Authentication (2FA), these plugins usually wait for the authentication phase to be completed before snooping on the authenticated session and stealing data to mount further attacks. Now we see more phishing attempts that can bypass two factor authentication (2FA) or multi-factor authentication, with Man-in-the-Middle attacks. Many with Two Factor Authentication (2FA) believe they’re protected because the birth of 2FA grew from knowing that current security defense solutions were no longer working.
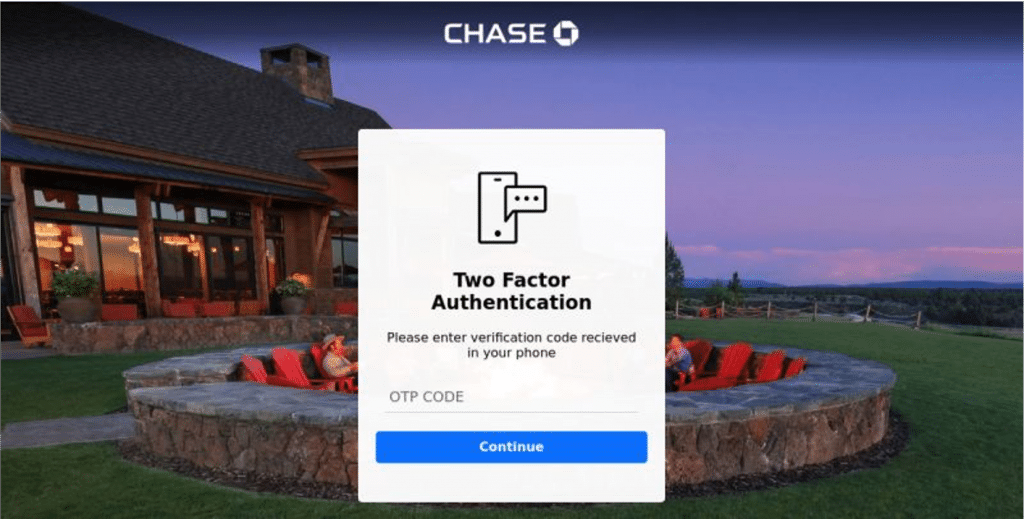
Example 1: A phishing site using reverse web proxy to hijack session cookies
SlashNext Blog | Man in the Middle Attacks

Today, while man-in-the-middle (MiTM) attacks are still a big concern, the security endpoint has changed to the browser, creating a MiTB phishing threat that poses real danger.

In recent years phishing has become the number one threat action over malware. Recent workforce changes spurred by the pandemic has led to an exponential increase in phishing attacks.

Just how prevalent are these phishing callbacks and C2 infections? In every client install we perform – 100 percent! – we see C2 infections and callbacks. Are you compromised?
In 2020 phishing exploded as the world faced a 100-year pandemic and many people moved to remote working and learning, which changed the phishing threat landscape forever.
It’s Time to Get Started with SlashNext
Learn how to leverage the industry’s best zero-hour phishing protection and IR solutions in your environment.
6701 Koll Center Parkway, Suite 250
Pleasanton CA 94566
800.930.8643
info@slashnext.com
© All Rights Reserved, SlashNext, Inc.



