Automate
Abuse Inbox Management
Simplify and expedite abuse inbox management and phishing incident response
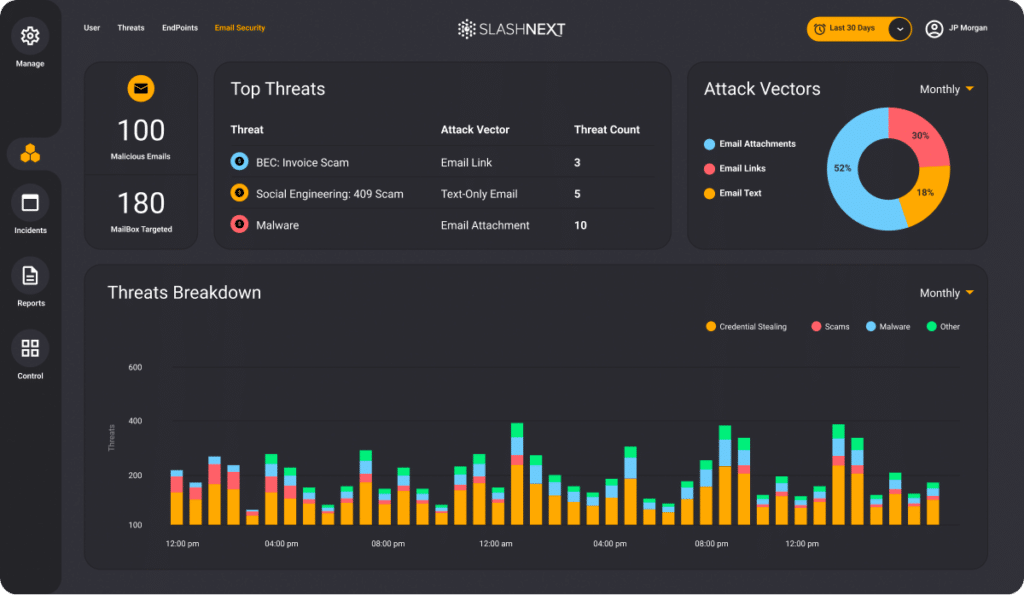
The Challenge
Effectively managing a growing abuse inbox with limited resources has become an increasing problem for SOC and IR teams. Automating URL analysis with SOAR playbooks has helped save time and resources but the efficacy of the automation is only as good as the threat intelligence and URL Analysis. Many services miss critical threats, that include:
Return false negatives on newer, previously unknown threats
Fail to identify URL obfuscation techniques, re-directs, and multi-stage attacks
Return inconclusive threat risk scores rather than accurate, definitive results
SlashNext Phishing Incident Response Advantage
Reduce the effort, and costs involved in abuse inbox management with accurate phishing URL analysis on-demand and at scale. Dynamic, run-time analysis uncovers live, previously unknown, zero-hour threats.
Improve Productivity and Save Money
Dramatically reduce the time and costs associated with researching suspicious URLs.
Live, Zero-Hour Detection
Broader Threat Detection
Detects all categories of phishing and social engineering threats including on legitimate infrastructure.
More Powerful Analysis
Detects zero-hour threats missed by URL inspection and domain reputation analysis methods.
Pre-Built Integrations
Overcomes Evasion Tactics
Detects threats using advanced evasion tactics like URL redirects, captchas, keyboard and mouse interaction.
URL Enrichment
With forensics, including screenshots, HTML, and rendered text.
Multiple IR Commands and Playbooks
Cover different reputation and enrichment use cases.
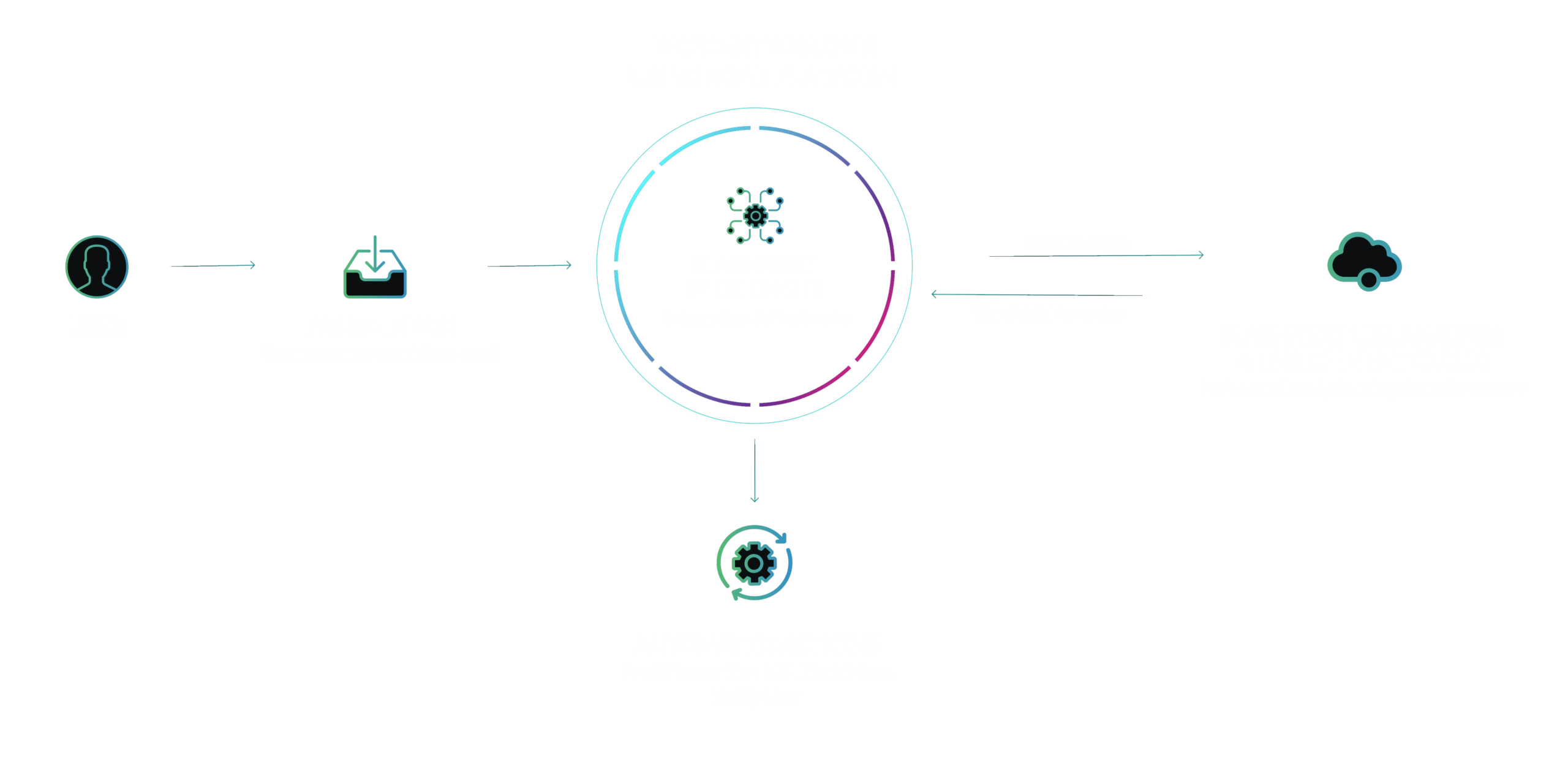
How it Works
Here’s an example phishing IR playbook for abuse inbox management. Pre-built integrations with leading SOAR platforms provide quick and easy operationalization of SlashNext Phishing URL Analysis & Enrichment.
See SlashNext Complete™ for Email, Mobile and Browser in Action
Meet with a security expert for a demo and learn how to set up a personalized trial to see the threats entering your organization.
6701 Koll Center Parkway, Suite 250
Pleasanton CA 94566
800.930.8643
info@slashnext.com
© All Rights Reserved, SlashNext, Inc.


