Expand Your Business with SlashNext
Grow your business by partnering with a leader in cloud email security with a channel-first, flexible, and profitable partner program.
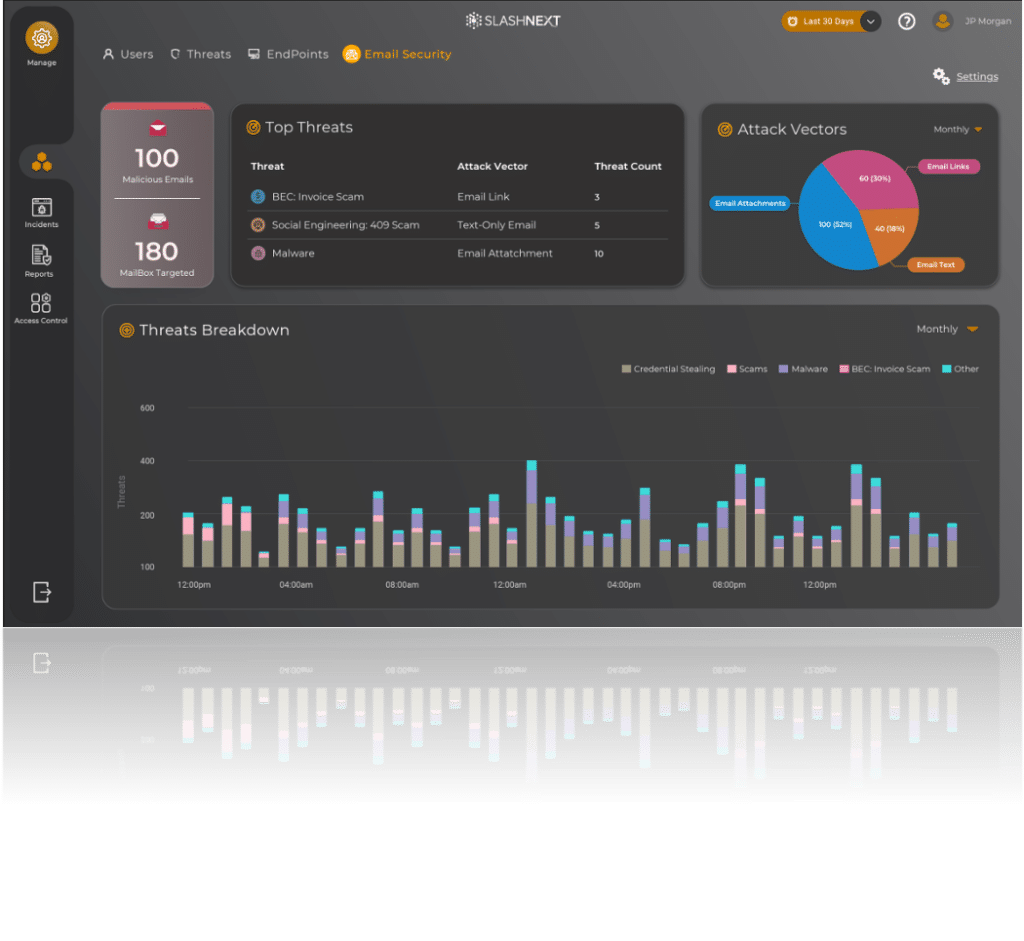
Why Partner with SlashNext?
- Ride the business wave away from SEGs to Integrated Cloud Email Security
- Sell the only platform that prevents advanced attacks on any messaging channel (email, SMS, Collaboration, Social)
- Utilize SlashNext Observability Risk Assessments to show immediate value from the first minute.
- Channel first, great margins, recurring revenue and high customer satisfaction
OUR CHANNEL FIRST APPROACH
Expand Your Business with SlashNext
We are channel-driven company. We are dedicated to enabling the channel to secure email, plus mobile and web messaging apps. As a partner, you have access to our sales tools, hands-on sales and technical support for your team, and channel investment marketing.
- Recurring revenue with upsell opportunities and solutions
- Partner protected renewals at same buy price and wholesale pricing based on volume driven MSRP
- Immediate time to value with quick setup and deployment, sales cycles less than 90 days and POV typically in 2 weeks
- Hands on support from SlashNext security professionals through the sales cycle
SlashNext Partners with Microsoft for Precision Security Solutions
SlashNext HumanAI™ stops BEC, credential stealing, malware and exploits that lead to business disruption, financial loss and customer trust.
It’s Time to Get Started with SlashNext
Let’s work together on our shared goals of stopping threats.
6701 Koll Center Parkway, Suite 250
Pleasanton CA 94566
800.930.8643
info@slashnext.com
© All Rights Reserved, SlashNext, Inc.





