SlashNext for Microsoft Sentinel
A simple way to see what is evading your current security defenses. The secure assessment is easy to run with Microsoft Sentinel weblogs and requires less than 10 minutes of setup time.
SlashNext and Microsoft for Defense-in-Depth Security
SlashNext HumanAI™ stops BEC, credential stealing, malware and exploits that lead to business disruption, financial loss and customer trust. Available on the Azure Marketplace and AppSource.
Start a Website Vulnerability Assessment Today
SlashNext’s patented detection technology preemptively identifies malicious URLs 48 hours ahead of other security vendors using virtual browsers and machine learning.
SlashNext with Microsoft Sentinel delivers instant value by automatically identifying malicious URLs with precision (high detection rate with low false positive rate). Enabling you to investigate, respond, and connect with other Microsoft Sentinel solutions and services to remediate newly discovered threats before they compromise your organization.
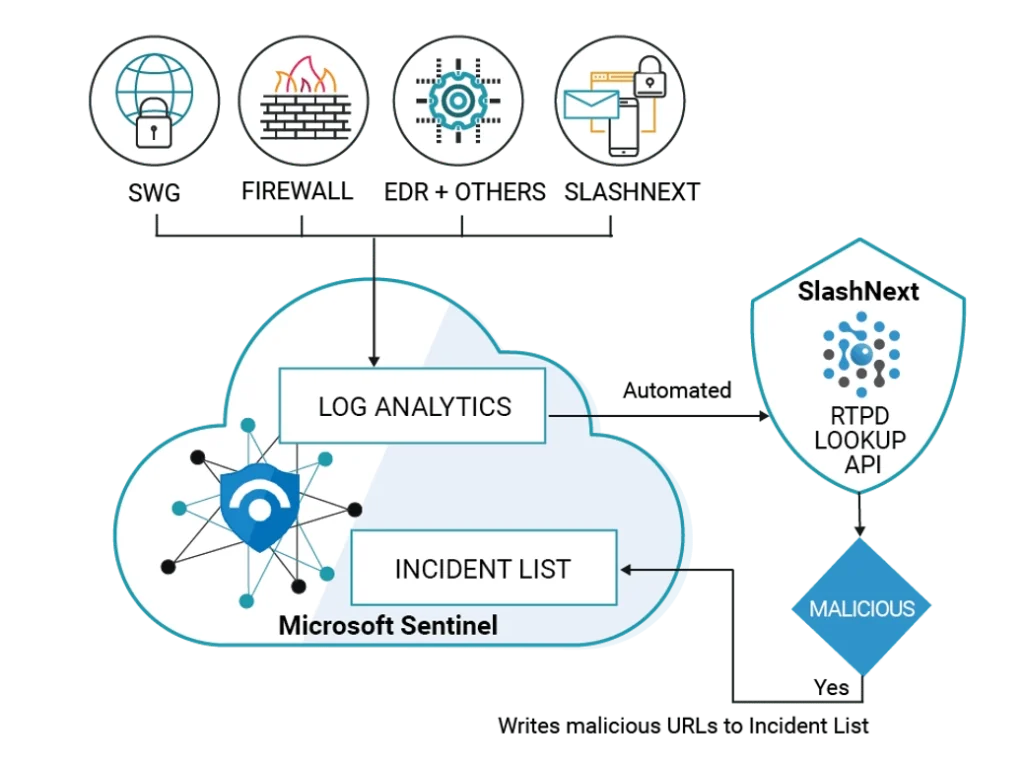
See SlashNext Complete™ for Email, Mobile and Browser in Action
Meet with a security expert for a demo and learn how to set up a personalized trial to see the threats entering your organization.
6701 Koll Center Parkway, Suite 250
Pleasanton CA 94566
800.930.8643
info@slashnext.com
© All Rights Reserved, SlashNext, Inc.




