Phishing Incident Response
Automate abuse mailbox management with accurate, run-time analysis of suspicious URLs on-demand.
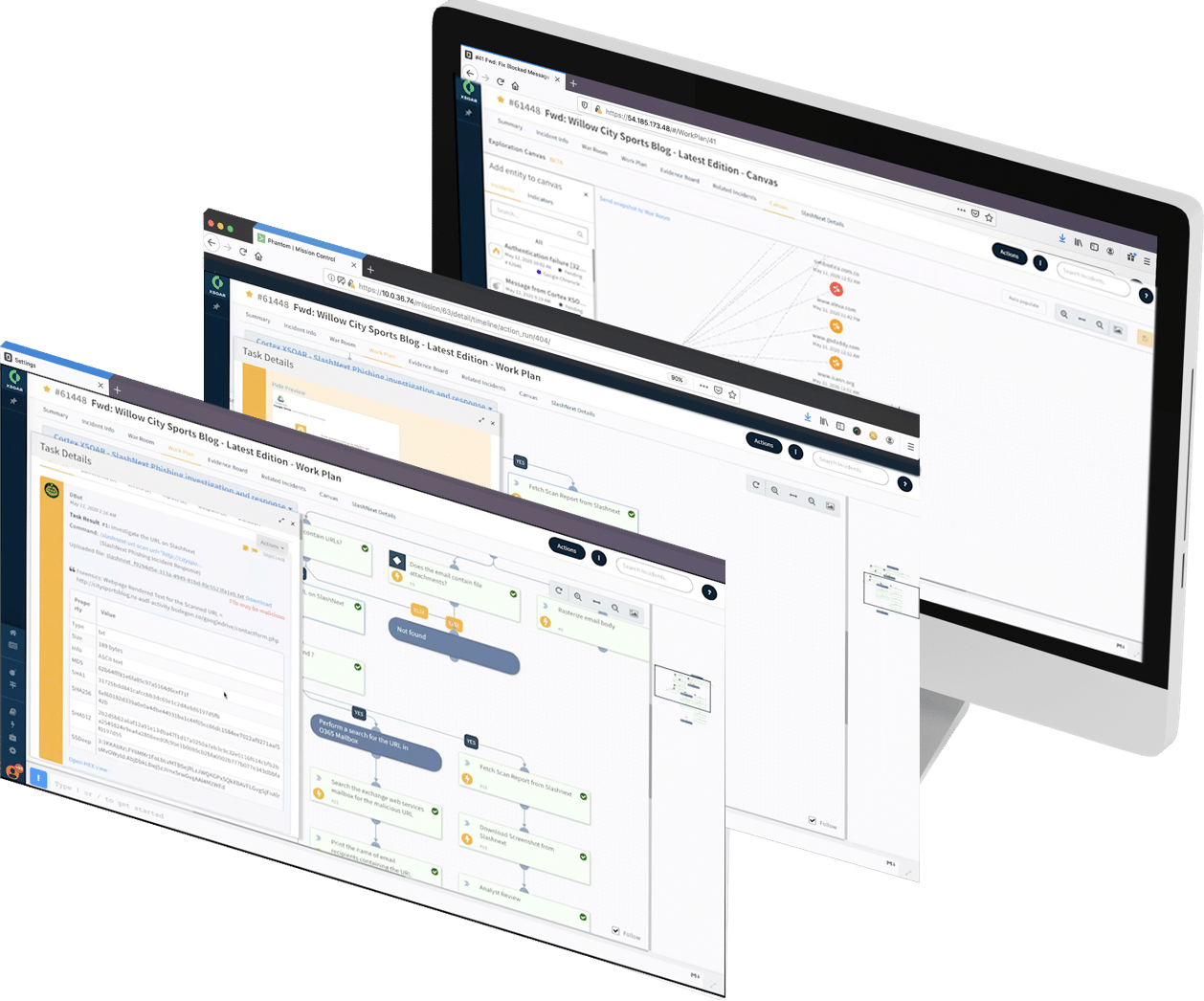
Phishing-Focused URL Analysis
Malware sandboxes are useful for analyzing malicious binaries and files using virtual machines, but they are not designed for analyzing phishing and social engineering web pages. SlashNext provides SOC and IR teams with a scalable, cloud-based analysis engine purpose-built for analyzing phishing URLs using virtual browsers and patented SEER™ threat detection technology.
Detects All Major Phishing Payloads
Unlike other phishing URL analysis technologies, which largely focus on identifying fake log-in pages for major brands, SlashNext detects all major phishing payload threats.
Credential Stealing
Fake log-in pages
Rogue Software
Rogue browser extensions, fake AVs, etc.
Document Theft
Document, IP, and media theft
Tech Support Scams
Fake virus alerts, pop-ups, on-line support scams
Money Transfer Scams
Wire transfers, Bitcoin, gift card, fake deals, etc.
Extreme Accuracy
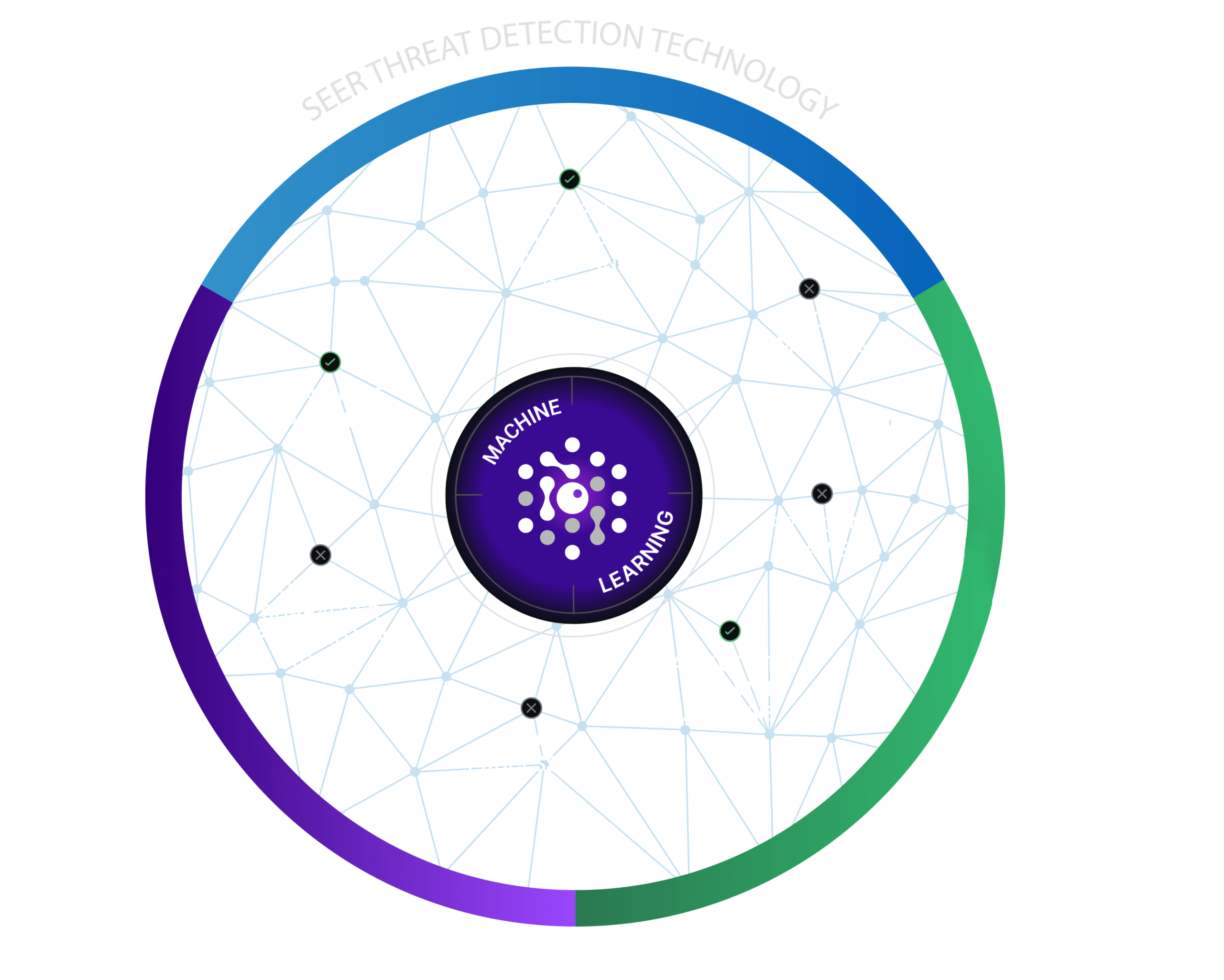
Perform runtime behavioral analysis on suspicious URLs/webpages using patented, cloud-powered SEER™ threat detection technology. SEER uses virtual browsers to dynamically analyze page contents (images, text etc.) and server behavior. Mature machine learning algorithms enable definitive, binary verdicts (not threat scores) with >99.95% precision.
Full Automation
URL Analysis & Enrichment is fully automated and needs no manual intervention. Just submit URLs to SlashNext cloud via automated playbook commands and get accurate, binary verdicts. Eliminate countless hours of analysis and further research on inconclusive results.
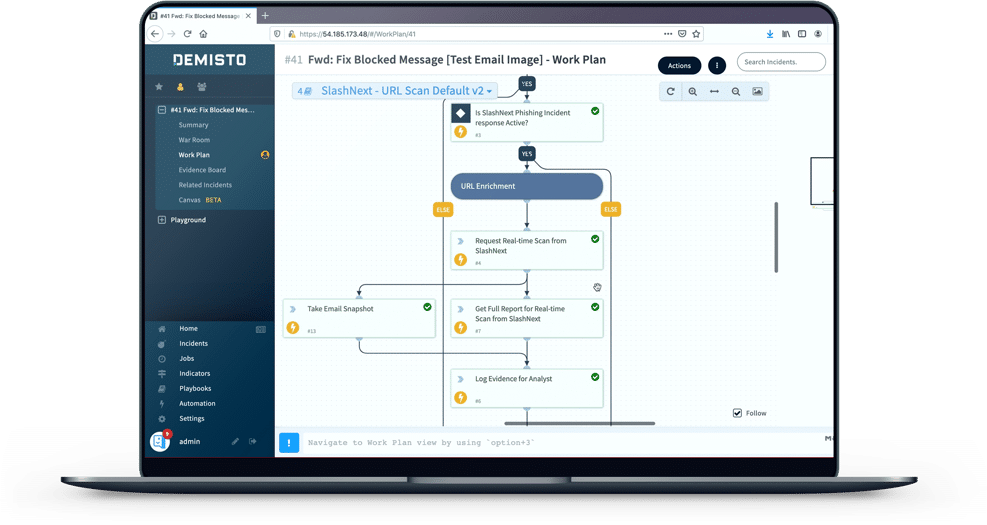
URL Enrichment
SlashNext enriches URLs with a definitive verdict plus forensics data, including screenshots, HTML, and rendered text combined with reporting artifacts. This simplifies phishing IR processes and reporting. IoCs such as screenshots can even aid in employee phishing training and testing programs.
Cloud Scale
SlashNext URL analysis operates at cloud scale, using millions of virtual browsers to analyze many millions of suspicious webpages daily. Analyze thousands, or even millions, of suspicious URLs on demand.
Zero-Hour Detection
SEER threat detection technology catches phishing threats missed by URL inspection and domain reputation technologies. With its patented approach, SEER follows all URL re-directs and multi-stage attacks to analyze final destination pages. This enables detection of phishing URLs/webpages hosted on compromised websites and legitimate hosting infrastructure.
Deployment Flexibility
As a cloud-powered, API-based service, SlashNext integrates with popular SOAR and SIEM platforms. Moreover, the security team can leverage our Linux utilities and SDK to build custom apps and automation workflows.
Key SlashNext Advantages
Extreme Accuracy
Patented SEER threat detection technology delivers binary verdicts (not threat scores) with near-zero false positives (>99.95 accuracy).
Live, Zero-Hour Detection
Dynamic, runtime URL analysis (not just checks against known threat databases) uncovers live, previously unknown, zero-hour threats.
Broader Threat Detection
Detects all six major categories of phishing and social engineering threats, not just fake login pages for major brands.
More Powerful Analysis
Detects zero-hour threats missed by URL inspection and domain reputation analysis methods.
Overcomes Evasion Tactics
Detects threats using advanced evasion tactics like URL redirects, captchas, keyboard and mouse interaction.
Pre-Built Integrations
Expedite phishing IR and threat hunting via integration apps with leading SOAR and SEIM platforms.
Related SlashNext Resources

The State of Phishing 2021
Phishing attacks are moving faster than defenses. By mid-2020, SlashNext Threat Labs saw the numb…

Tolly Group Test Finds SlashNext’s 98.1% Spear Phishing Detection Rate Highest Among Key Security...
The results of the Tolly Group test demonstrates the difficulty for 1.0 anti-phishing solutions t…

AI Leads the Trend in Technologies to Fill the Cybersecurity Skills Shortage
As the shortage of skilled cybersecurity professionals intersects with the change and sophisticat…

Mobile Phishing Protection Data Sheet
SlashNext Mobile Phishing Protection provides the industry’s strongest protection against zero-ho…
Get Started with SlashNext Real-Time Phishing Forensics APIs
Get 50 scans a day for free to harness the power of real-time AI for the protection you need to hunt sophisticated phishing threats.










