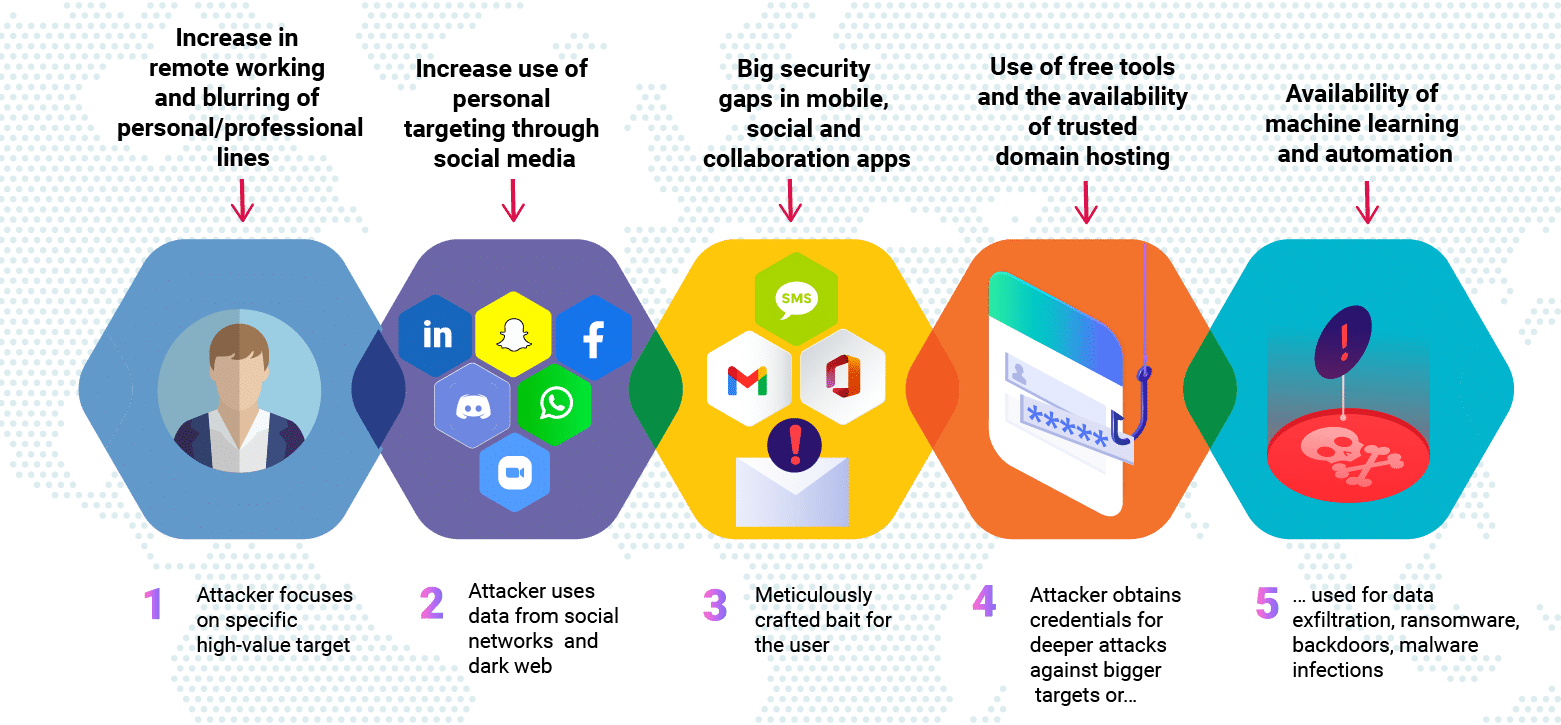
Spear Phishing
Phishing is most are familiar as mass emails that try to encourage someone to do something – from download an attachment, to click through to a website, to complete a form. In all these cases, once a recipient does one of these things, malware is installed that compromises the security of the computer system or network. These types of threats are becoming more and more sophisticated as emails and websites are designed to look more and more like established and trusted brands. Here enters spear phishing.
Anatomy of a Spear Phishing Attack
SlashNext Threat Labs observed a flurry of spear-phishing attacks targeting companies at the forefront of Covid-19 vaccines and therapeutics development. There were more than 800 spear phishing domains launched over 60 days that belong to the same threat actors. In all cases, these attacks point to Office 365 log-in pages. These spear-phishing attacks are designed to appear trustworthy. They are targeting specific individuals, in this case, companies that are working on Covid-19 vaccines or therapeutics in an attempt to steal sensitive account credentials.
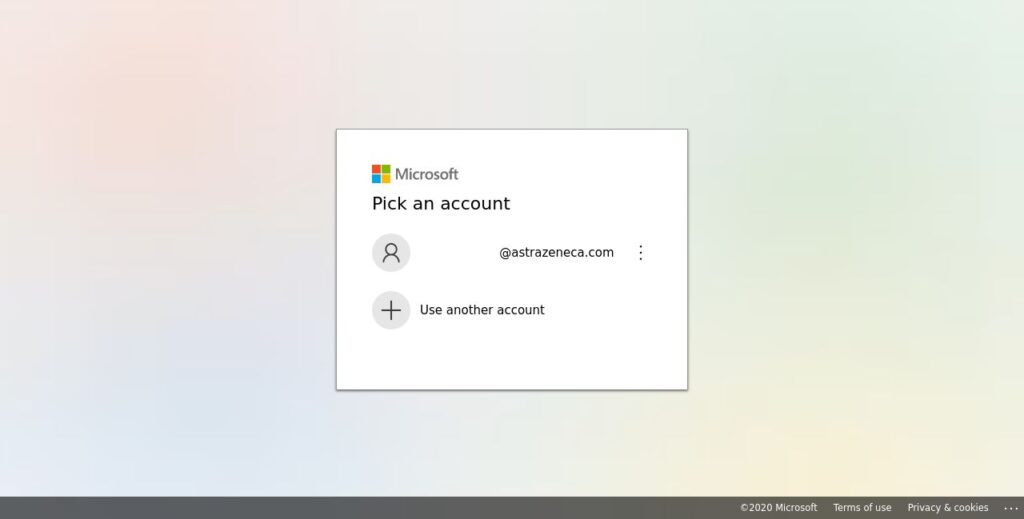
Example: Screenshot of fake Microsoft Office 365 page for AstraZeneca
SlashNext Blog | Spear Phishing

Today, while man-in-the-middle (MiTM) attacks are still a big concern, the security endpoint has changed to the browser, creating a MiTB phishing threat that poses real danger.

In recent years phishing has become the number one threat action over malware. Recent workforce changes spurred by the pandemic has led to an exponential increase in phishing attacks.

Just how prevalent are these phishing callbacks and C2 infections? In every client install we perform – 100 percent! – we see C2 infections and callbacks. Are you compromised?
In 2020 phishing exploded as the world faced a 100-year pandemic and many people moved to remote working and learning, which changed the phishing threat landscape forever.
Experience SlashNext Protection in Action
Request a free trial to see how SlashNext detects zero-hour threats in real-time and stop the attacks that impact your business.
6701 Koll Center Parkway, Suite 250
Pleasanton CA 94566
800.930.8643
info@slashnext.com
© All Rights Reserved, SlashNext, Inc.



