SlashNext Blog
Phishing, social engineering, and modern threats.
Featured Article
From Caesar to Cyberspace: The Growing Menace of Obfuscated Phishing Scams
In the world of cybersecurity, it often feels like we’re revisiting familiar problems, albeit with a modern twist. The essence of the issue isn’t about the emergence of entirely new types of cyberattacks but rather how attackers ingeniously reinvent old tactics. A prime example of this is obfuscation—a method deeply rooted in the annals of […]
Featured Article
10 Ways URL Analysis & Enrichment Can Help Ease Your SOC’s Challenges in 2020
On-demand phishing URL analysis solutions can help ease your SOC teams’ pain and challenges.
Blog Subscription

From Caesar to Cyberspace: The Growing Menace of Obfuscated Phishing Scams
In the world of cybers…

Evolving Cyber Threats: Insights and Strategies from the 2023 FBI IC3 Report
Latest FBI IC3 Report …

Threat Actors are Exercising New Attack Techniques to Bypass Machine Learning Security Controls
“Conversation Ov…
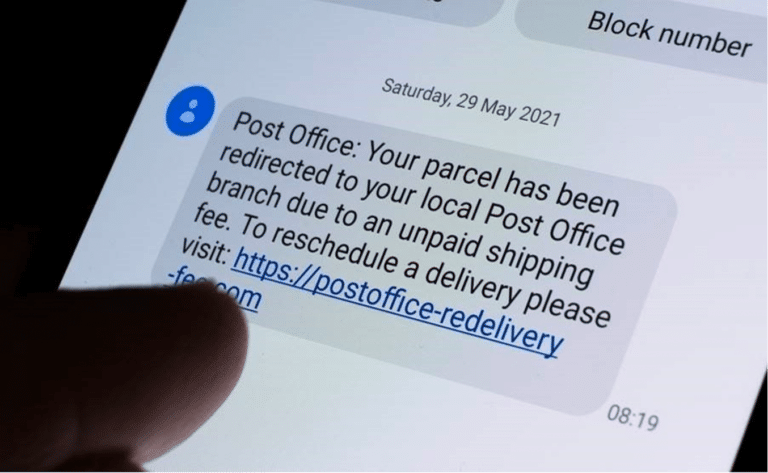
SMS Gateways Allow Cybercriminals to Flood Phones With SMS Phishing Messages For Just €0.004 ($0....
Our team has been inve…

Silent, Yet Powerful Pandora hVNC, The Popular Cybercrime Tool That Flies Under the Radar
Pandora hVNC is a remo…

Malicious Use of QR Codes on the Rise Through Quishing Attacks
Quick Response codes –…
Scam or Mega Chatbot? Investigating the New AI Chatbot Called Abrax666
An in-depth investigat…
AI-Based Cybercrime Tools WormGPT and FraudGPT Could Be The Tip of the Iceberg
The rise of AI-powered…
It’s Time to Get Started with SlashNext
Learn how to leverage the industry’s best zero-hour phishing protection in your environment.
6701 Koll Center Parkway, Suite 250
Pleasanton CA 94566
800.930.8643
info@slashnext.com
© All Rights Reserved, SlashNext, Inc.






