Credential Stealing
The goal of credential theft is to attain passwords with the intent to access protected data.
Credential Stealing is one of the oldest form of phishing attacks. Stealing credentials is the first stage in ransomware, malware or data exfiltration attacks. This type of attack tricks the user into giving up their credentials by representing a near-copy of a legitimate web page. Replica pages often leverage popular global brands such as Google, Microsoft, Dropbox, and Yahoo for credential stealing attacks. Some come complete with functional “Password Reset” options, and some ask for secondary email accounts, mobile phone numbers, or security questions for “enhanced security”. These attacks are effective because the user usually can’t differentiate between the fake and legitimate page. Virtually any brand can be easily impersonated, and the inherent trust that the brand has created with its customers is the very thing that attackers use to their advantage.

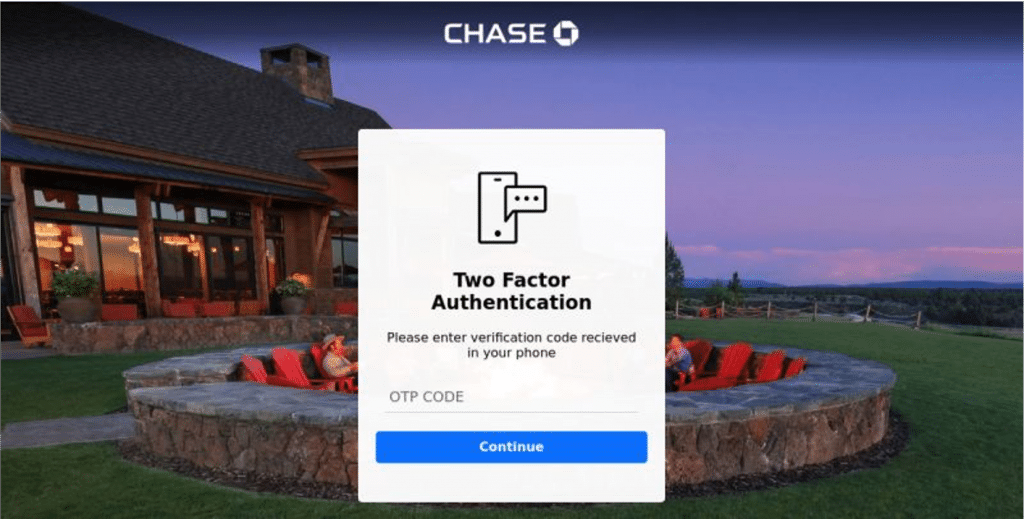
Example: A spoofed site using 2FA to cover for the malicious URL
Enterprises have tried to reduce their risk to these sorts of attacks by training their employees on how to identify and avoid these kinds of fake sign-in pop-ups and pages. However, despite training, humans make mistakes. Phishing is so sophisticated today it can easily emulate the authentication websites themselves. Unsuspecting users have presented a login experience that looks just like their normal 2FA experience but is actually a fake site that captures their authentication codes and user credentials. While the actual session token is not compromised, the user is tricked into providing additional security credentials or qualifying data that they might normally provide in a password recovery experience. This data can then be used by bad actors to access one or more corporate systems.
What You Can Do to Protect Yourself
Harness the power of artificial intelligence (AI) and machine learning (ML) – and then bolster it. These technologies excel at spotting anomalous behavior and reacting swiftly in response. Using natural language and link-based detection, they can protect users from email phishing, mobile-based smishing (SMS phishing), browser-based spear-phishing (targeted phishing), and business email compromise (when criminals intercept company correspondence and insert malicious information, such as different bank payment details).
By harnessing AI and ML, we can secure browsers and preemptively stop attacks that target users such as employees or customers. We then also solve the conundrum of keeping digital interactions secure in a world where the browser is our operating system.
Rather than reinvent the software wheel, a little computer intelligence and vigilance can go a long way and resolve the browser security paradox.
SlashNext Email Protection for Microsoft365 stops 65% more spear-phishing, BEC, malware, and ransomware link threats than all other cloud-native email security services. SlashNext zero-hour protection in real-time through patented AI-powered detection delivers a 99.9% detection rate with Live Scan identifying zero-hour threats in real-time. Incredibly quick time to value with the first incident identified in 1 hour or less and protection against phishing emails using URLs trusted domains that evade SEG technology
SlashNext Blog | Credential Stealing

Today, while man-in-the-middle (MiTM) attacks are still a big concern, the security endpoint has changed to the browser, creating a MiTB phishing threat that poses real danger.

In recent years phishing has become the number one threat action over malware. Recent workforce changes spurred by the pandemic has led to an exponential increase in phishing attacks.

Just how prevalent are these phishing callbacks and C2 infections? In every client install we perform – 100 percent! – we see C2 infections and callbacks. Are you compromised?
In 2020 phishing exploded as the world faced a 100-year pandemic and many people moved to remote working and learning, which changed the phishing threat landscape forever.
It’s Time to Get Started with SlashNext
Learn how to leverage the industry’s best zero-hour phishing protection and IR solutions in your environment.
6701 Koll Center Parkway, Suite 250
Pleasanton CA 94566
800.930.8643
info@slashnext.com
© All Rights Reserved, SlashNext, Inc.



